Operational Technology (OT) Security Market Size 2026-2030
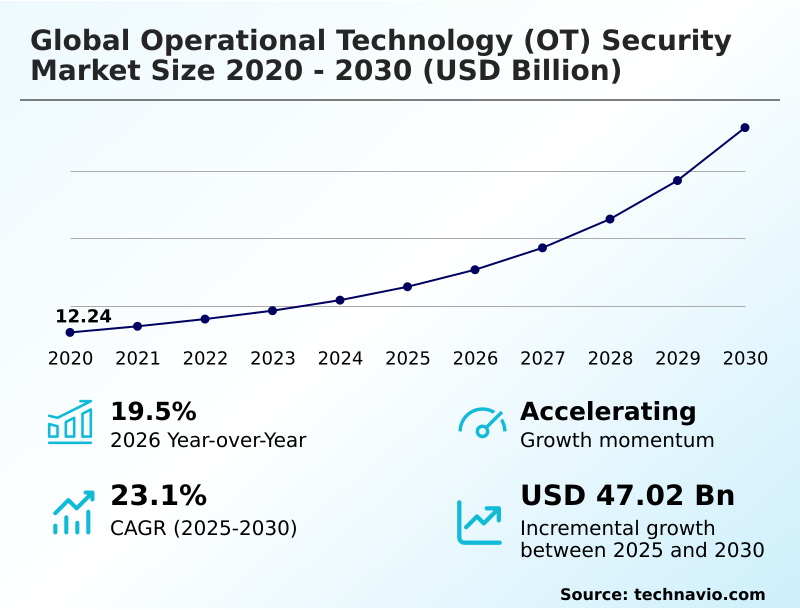
The operational technology (ot) security market size is valued to increase by USD 47.02 billion, at a CAGR of 23.1% from 2025 to 2030. Surge in sophisticated cyberattacks on critical infrastructure will drive the operational technology (ot) security market.
Major Market Trends & Insights
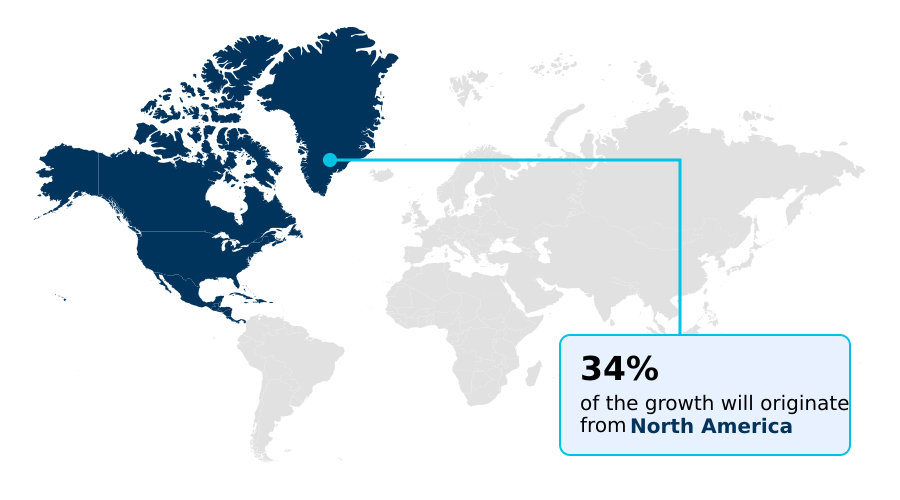
- North America dominated the market and accounted for a 33.9% growth during the forecast period.
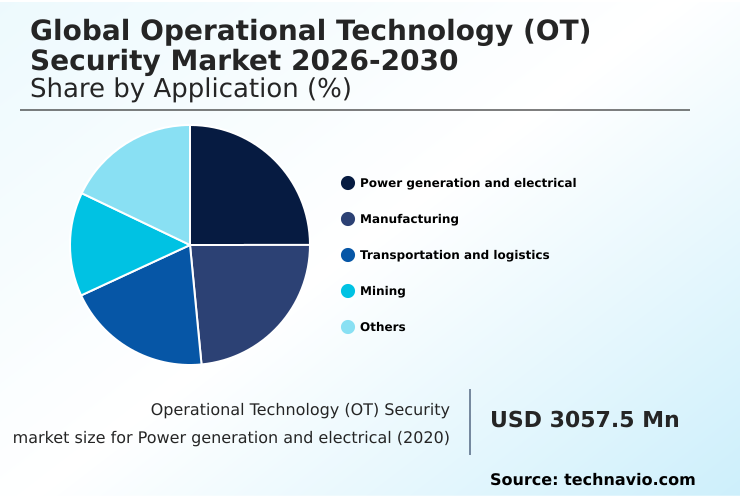
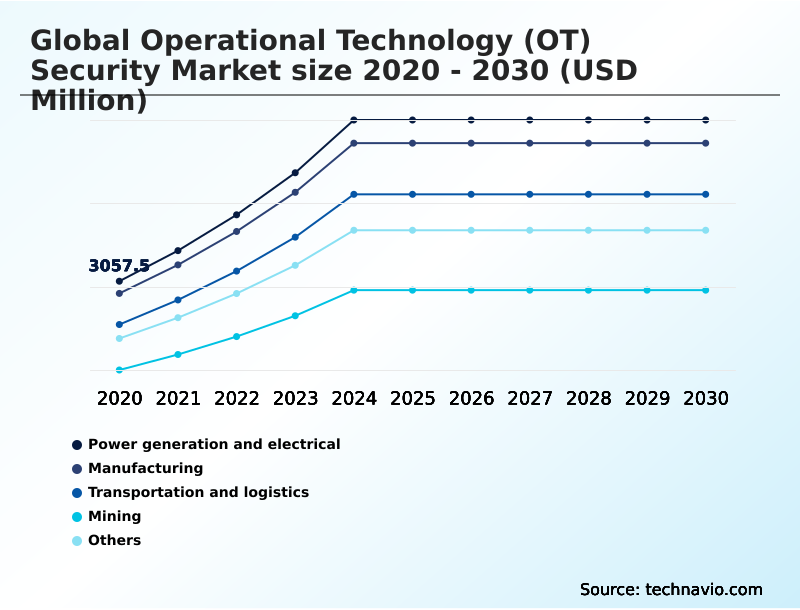
- By Application - Power generation and electrical segment was valued at USD 5.50 billion in 2024
- By End-user - SMEs segment accounted for the largest market revenue share in 2024
Market Size & Forecast
- Market Opportunities: USD 60.52 billion
- Market Future Opportunities: USD 47.02 billion
- CAGR from 2025 to 2030 : 23.1%
Market Summary
- The operational technology (OT) security market is defined by the imperative to protect industrial processes and critical infrastructure from digital threats. As industries embrace digital transformation, the convergence of information technology and OT networks exposes previously isolated systems, such as industrial control systems (ICS) and SCADA, to significant cyber risks.
- This integration, while boosting efficiency, creates a larger attack surface that malicious actors can exploit. Key drivers include the rise of Industry 4.0, which mandates connectivity for data analytics and remote operations, and stringent government regulations requiring compliance with security standards.
- For instance, a modern manufacturing facility leveraging IIoT sensors for predictive maintenance must ensure the integrity of its data flow from the factory floor to the cloud. A breach could not only halt production but also lead to physical damage or safety incidents.
- Consequently, organizations are compelled to adopt specialized security solutions that can monitor proprietary industrial protocols and segment critical assets, addressing the unique challenges of securing legacy and modern cyber-physical systems in a hyper-connected environment.
What will be the Size of the Operational Technology (OT) Security Market during the forecast period?
Get Key Insights on Market Forecast (PDF) Request Free Sample
How is the Operational Technology (OT) Security Market Segmented?
The operational technology (ot) security industry research report provides comprehensive data (region-wise segment analysis), with forecasts and estimates in "USD million" for the period 2026-2030, as well as historical data from 2020-2024 for the following segments.
- Application
- Power generation and electrical
- Manufacturing
- Transportation and logistics
- Mining
- Others
- End-user
- SMEs
- Large enterprises
- Deployment
- On-premises
- Cloud
- Hybrid
- Geography
- North America
- US
- Canada
- Mexico
- APAC
- China
- Japan
- India
- Europe
- Germany
- UK
- France
- Middle East and Africa
- Saudi Arabia
- UAE
- South Africa
- South America
- Brazil
- Argentina
- Rest of World (ROW)
- North America
By Application Insights
The power generation and electrical segment is estimated to witness significant growth during the forecast period.
The power generation and electrical segment faces heightened security demands as grid modernization accelerates. Protecting these cyber-physical systems is critical, with a focus on securing distributed control systems and legacy industrial systems against disruption.
Key strategies include proactive threat intelligence integration and robust endpoint protection to safeguard assets. The implementation of OT network monitoring is essential for maintaining operational resilience in an environment where attacks have impacted nearly 70% of organizations in related industries.
Effective industrial cybersecurity compliance requires advanced tools to defend critical infrastructure and ensure the stability of the energy sector, addressing vulnerabilities in both modern and aging assets.
The Power generation and electrical segment was valued at USD 5.50 billion in 2024 and showed a gradual increase during the forecast period.
Regional Analysis
North America is estimated to contribute 33.9% to the growth of the global market during the forecast period.Technavio’s analysts have elaborately explained the regional trends and drivers that shape the market during the forecast period.
See How Operational Technology (OT) Security Market Demand is Rising in North America Request Free Sample
The global geographic landscape for operational technology security is shaped by distinct regional drivers. In North America, stringent regulatory actions, including new directives for maritime and port security, are compelling investments in advanced threat detection and OT asset discovery.
Meanwhile, APAC is advancing its defensive posture with strategic roadmaps like Singapore's Cybersecurity Masterplan, which promotes secure-by-deployment principles. In Europe, the NIS2 Directive is fundamentally altering compliance requirements, mandating stricter risk management across energy, transport, and manufacturing sectors.
The urgency is underscored by data showing that over 70% of inspected water systems in one major region failed to meet basic security standards.
Consequently, the adoption of unified IT/OT security platforms has increased by 50% in regulated industries, reflecting a global move toward integrated and resilient industrial defense.
Market Dynamics
Our researchers analyzed the data with 2025 as the base year, along with the key drivers, trends, and challenges. A holistic analysis of drivers will help companies refine their marketing strategies to gain a competitive advantage.
- Achieving robust industrial security requires a multi-faceted strategy beginning with establishing IT-OT convergence security best practices to bridge the gap between corporate and plant environments. A critical element of this is securing legacy OT assets from ransomware, which often involves a combination of virtual patching and network isolation.
- For organizations operating within the European Union, compliance with NIS2 directive for OT is non-negotiable, necessitating rigorous risk assessments and incident reporting. The modern approach to defense increasingly involves zero trust implementation in manufacturing OT, which ensures that no user or device is trusted by default. This method is central to effective cyber risk management for industrial networks.
- At a granular level, protecting PLCs and HMIs from attacks requires deep packet inspection and protocol-aware security controls. These efforts are supported by OT network segmentation for critical infrastructure, which contains threats and prevents lateral movement. A foundational step is a thorough vulnerability assessment for industrial environments, complemented by a continuous OT asset inventory and management strategy.
- Additionally, organizations must implement secure remote access for third-party vendors and develop comprehensive incident response planning for OT environments. Proactive measures, such as threat hunting in operational technology networks, are essential for implementing a secure OT architecture and reducing attack surface in smart factories.
- Enterprises that adopt these layered strategies have demonstrated a twofold improvement in detecting internal threats compared to those with only perimeter defenses, particularly in OT security for power generation facilities and in addressing cybersecurity measures for transportation logistics, thereby achieving OT compliance with government regulations while managing security in hybrid IT-OT SOCs and defending against state-sponsored OT attacks to ensure safety in automated industrial systems.
What are the key market drivers leading to the rise in the adoption of Operational Technology (OT) Security Industry?
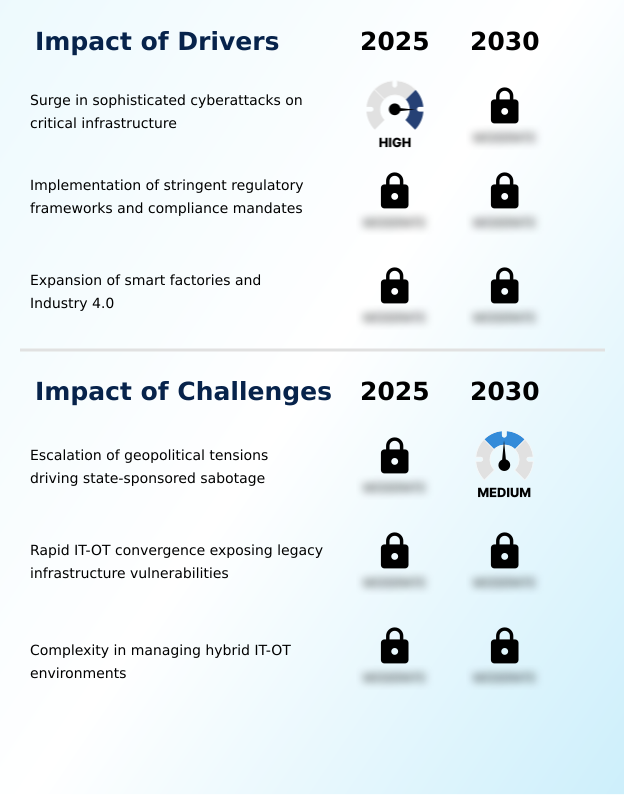
- The increasing frequency and sophistication of cyberattacks targeting critical infrastructure serves as a primary driver for the operational technology security market.
- Market growth is significantly fueled by the expansion of Industry 4.0 and the proliferation of smart factories. This digital transformation, while improving efficiency, introduces vulnerabilities that require advanced manufacturing cybersecurity solutions and a focus on OT security risk assessment.
- The increasing sophistication of cyberattacks targeting industrial operations necessitates a proactive defense posture, driving demand for solutions that ensure operational resilience. Furthermore, stringent government regulations mandating critical infrastructure protection are compelling organizations to invest in technologies for OT network monitoring.
- These drivers have led to a 75% increase in the adoption of automated compliance reporting tools, while organizations that implement proactive defense strategies report a 40% faster incident response time compared to those with reactive measures.
What are the market trends shaping the Operational Technology (OT) Security Industry?
- A growing dependence on the internet for industrial processes is a primary market trend. This heightened connectivity exposes previously isolated operational technology to a range of new cyber threats.
- Key trends are reshaping the industrial security landscape, driven by the convergence of IT and OT environments. This integration demands unified security architectures that can provide OT asset discovery and manage industrial cybersecurity compliance across the entire enterprise. As organizations increasingly depend on internet connectivity for remote monitoring and data analytics, implementing a robust IIoT security framework has become critical.
- This digital shift supports smart factory security initiatives but also expands the attack surface, making systems more vulnerable. Consequently, there is a growing reliance on platforms that offer a single view of both IT and OT assets.
- Adoption of these unified platforms has risen by 45% in the manufacturing sector as companies prioritize a holistic approach to Industry 4.0 cybersecurity, improving threat visibility by over 60%.
What challenges does the Operational Technology (OT) Security Industry face during its growth?
- The escalation of geopolitical tensions, which fuels state-sponsored cyber sabotage against industrial targets, presents a significant challenge for the operational technology security market.
- A primary challenge in the market is the complexity of securing converged networks where legacy industrial systems meet modern IT infrastructure. Many industrial control systems (ICS) and distributed control systems lack native security features, creating significant vulnerabilities when connected to corporate networks.
- This issue is compounded by the difficulty in applying traditional IT security measures, such as patching, without risking operational disruption, which can delay vulnerability remediation by up to 50% in critical environments. Managing security in a hybrid ecosystem with conflicting priorities—uptime for OT versus frequent updates for IT—requires specialized OT security governance and tools.
- Organizations often struggle with a lack of visibility into their OT assets, with reports indicating that as many as 30% of devices on industrial networks are unmanaged or unidentified, complicating OT incident response.
Exclusive Technavio Analysis on Customer Landscape
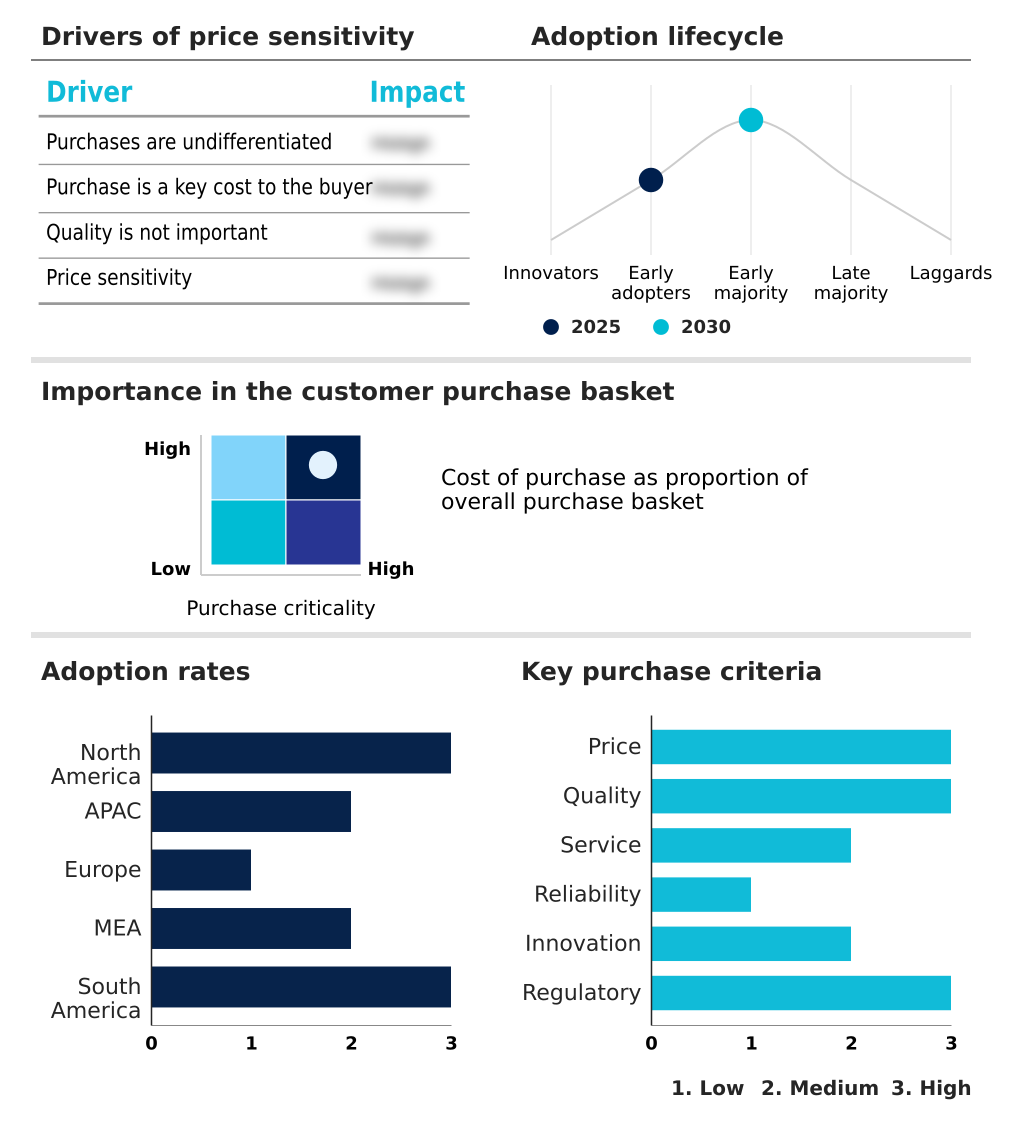
The operational technology (ot) security market forecasting report includes the adoption lifecycle of the market, covering from the innovator’s stage to the laggard’s stage. It focuses on adoption rates in different regions based on penetration. Furthermore, the operational technology (ot) security market report also includes key purchase criteria and drivers of price sensitivity to help companies evaluate and develop their market growth analysis strategies.
Customer Landscape of Operational Technology (OT) Security Industry
Competitive Landscape
Companies are implementing various strategies, such as strategic alliances, operational technology (ot) security market forecast, partnerships, mergers and acquisitions, geographical expansion, and product/service launches, to enhance their presence in the industry.
AO Kaspersky Lab - Key offerings provide specialized protection for industrial environments, focusing on threat detection, network visibility, and enforcing zero-trust security principles across converged IT/OT assets.
The industry research and growth report includes detailed analyses of the competitive landscape of the market and information about key companies, including:
- AO Kaspersky Lab
- BeyondTrust Corp.
- Broadcom Inc.
- Check Point Software Tech Ltd.
- Cisco Systems Inc.
- CyberArk Software Ltd.
- Darktrace Holdings Ltd.
- Forcepoint LLC
- Forescout Technologies Inc.
- Fortinet Inc.
- Fortra LLC
- Microsoft Corp.
- Nozomi Networks Inc.
- Okta Inc.
- Palo Alto Networks Inc.
- Radiflow
- Sophos Ltd.
- Tenable Holdings Inc.
- Zscaler Inc.
Qualitative and quantitative analysis of companies has been conducted to help clients understand the wider business environment as well as the strengths and weaknesses of key industry players. Data is qualitatively analyzed to categorize companies as pure play, category-focused, industry-focused, and diversified; it is quantitatively analyzed to categorize companies as dominant, leading, strong, tentative, and weak.
Recent Development and News in Operational technology (ot) security market
- In August, 2024, Claroty announced a strategic collaboration with Amazon Web Services to help organizations enhance cyber and operational resilience by combining cloud scalability with specialized cyber-physical systems protection.
- In October, 2024, Palo Alto Networks Inc. launched new solutions powered by Precision AI, including guided virtual patching and a secure browser, to bolster security for remote industrial operations.
- In November, 2024, Zscaler Inc. introduced a Zero Trust Segmentation solution designed to replace traditional firewalls in factories and branches, preventing lateral threat movement within critical infrastructure.
- In March, 2025, Fortinet Inc. announced significant updates to its operational technology security platform, introducing ruggedized hardware and enhancing its cloud-based, AI-driven threat hunting capabilities for hybrid environments.
Dive into Technavio’s robust research methodology, blending expert interviews, extensive data synthesis, and validated models for unparalleled Operational Technology (OT) Security Market insights. See full methodology.
| Market Scope | |
|---|---|
| Page number | 304 |
| Base year | 2025 |
| Historic period | 2020-2024 |
| Forecast period | 2026-2030 |
| Growth momentum & CAGR | Accelerate at a CAGR of 23.1% |
| Market growth 2026-2030 | USD 47019.1 million |
| Market structure | Fragmented |
| YoY growth 2025-2026(%) | 19.5% |
| Key countries | US, Canada, Mexico, China, Japan, India, South Korea, Australia, Indonesia, Germany, UK, France, Italy, Spain, The Netherlands, Saudi Arabia, UAE, South Africa, Israel, Turkey, Brazil, Argentina and Chile |
| Competitive landscape | Leading Companies, Market Positioning of Companies, Competitive Strategies, and Industry Risks |
Research Analyst Overview
- The operational technology (OT) security market is fundamentally centered on protecting industrial control systems (ICS) and ensuring SCADA security for critical infrastructure. As cyber-physical systems become more interconnected, the need for robust security is paramount. Key defense strategies include network segmentation and the deployment of an industrial demilitarized zone (IDMZ) to isolate process control networks (PCN).
- Solutions increasingly incorporate a zero trust architecture, moving beyond perimeter defense to verify every transaction. Advanced anomaly detection is crucial for identifying malicious activity within proprietary industrial protocols, while comprehensive asset inventory management provides the necessary visibility for effective vulnerability management. Protecting programmable logic controllers (PLCs) and human-machine interfaces (HMIs) requires tailored endpoint protection.
- Leading firms focus on providing OT threat detection through continuous OT network monitoring and industrial firewalls. Technologies like data diodes enforce one-way data flow, while secure remote access (SRA) governs third-party connections.
- Ultimately, the goal is achieving operational resilience and cyber-physical systems protection, with organizations leveraging threat intelligence integration to improve their defensive posture, resulting in a 30% reduction in incident discovery times. Safeguarding safety instrumented systems (SIS) remains a top priority, ensuring that cyber threats do not escalate into physical safety events.
What are the Key Data Covered in this Operational Technology (OT) Security Market Research and Growth Report?
-
What is the expected growth of the Operational Technology (OT) Security Market between 2026 and 2030?
-
USD 47.02 billion, at a CAGR of 23.1%
-
-
What segmentation does the market report cover?
-
The report is segmented by Application (Power generation and electrical, Manufacturing, Transportation and logistics, Mining, and Others), End-user (SMEs, and Large enterprises), Deployment (On-premises, Cloud, and Hybrid) and Geography (North America, APAC, Europe, Middle East and Africa, South America)
-
-
Which regions are analyzed in the report?
-
North America, APAC, Europe, Middle East and Africa and South America
-
-
What are the key growth drivers and market challenges?
-
Surge in sophisticated cyberattacks on critical infrastructure, Escalation of geopolitical tensions driving state-sponsored sabotage
-
-
Who are the major players in the Operational Technology (OT) Security Market?
-
AO Kaspersky Lab, BeyondTrust Corp., Broadcom Inc., Check Point Software Tech Ltd., Cisco Systems Inc., CyberArk Software Ltd., Darktrace Holdings Ltd., Forcepoint LLC, Forescout Technologies Inc., Fortinet Inc., Fortra LLC, Microsoft Corp., Nozomi Networks Inc., Okta Inc., Palo Alto Networks Inc., Radiflow, Sophos Ltd., Tenable Holdings Inc. and Zscaler Inc.
-
Market Research Insights
- Market dynamics are shaped by an urgent need for critical infrastructure protection, driving investments in industrial cybersecurity compliance and robust OT security risk assessment. The adoption of an IIoT security framework is essential for smart factory security, while government-led initiatives like maritime cybersecurity standards and water utility security mandates enforce higher defense postures.
- Organizations are developing a comprehensive OT cybersecurity maturity model to guide their strategies. This focus on defending critical infrastructure has led to a greater emphasis on manufacturing cybersecurity solutions and energy sector cyber defense. To achieve this, enterprises are securing converged networks and using cyber-physical threat intelligence for proactive defense.
- Effective OT security governance and OT incident response plans are now standard practice, with supply chain cybersecurity becoming a critical focus. This strategic shift improves breach detection by over 40% and reduces compliance reporting overhead by 25%.
We can help! Our analysts can customize this operational technology (ot) security market research report to meet your requirements.