Cloud Workload Protection Market Size 2024-2028
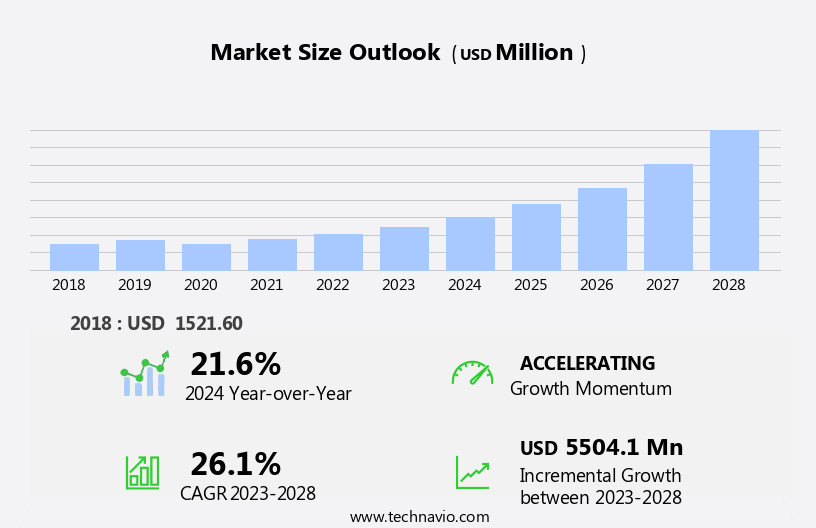
The cloud workload protection market size is forecast to increase by USD 5.5 billion at a CAGR of 26.1% between 2023 and 2028.
What will be the Size of the Cloud Workload Protection Market During the Forecast Period?
How is this Cloud Workload Protection Industry segmented and which is the largest segment?
The cloud workload protection industry research report provides comprehensive data (region-wise segment analysis), with forecasts and estimates in "USD million" for the period 2024-2028, as well as historical data from 2018-2022 for the following segments.
- Deployment
- Hybrid
- Public
- Private
- Geography
- North America
- US
- Europe
- Germany
- UK
- APAC
- China
- Japan
- Middle East and Africa
- South America
- North America
By Deployment Insights
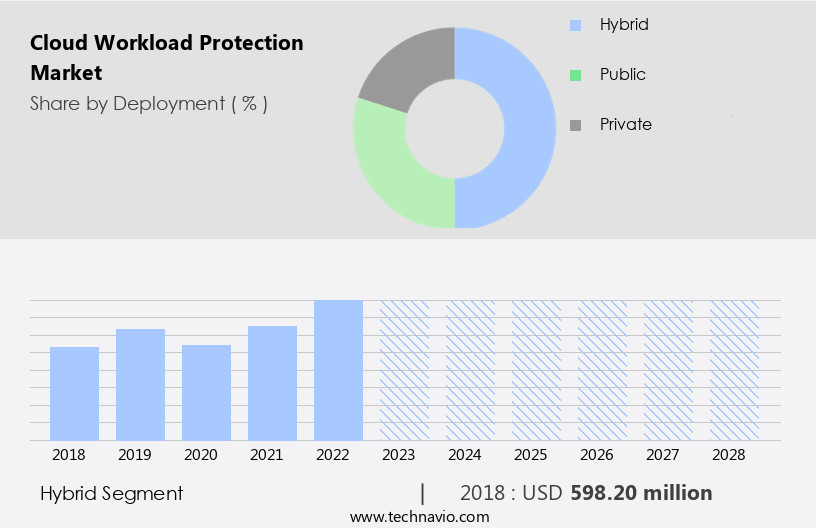
- The hybrid segment is estimated to witness significant growth during the forecast period.
Cloud technologies are transforming business operations by reducing expenses and enabling flexible provisioning for organizations worldwide. In the market, hybrid deployment models dominate, accounting for the largest revenue share. Hybrid cloud workloads represent a combination of private and public cloud deployments, offering benefits such as data sharing, cost efficiency, scalability, and security. The adoption of hybrid cloud workloads is expected to continue growing due to their ability to prioritize business needs over infrastructure costs. Hybrid cloud environments provide enhanced security features, including threat detection, vulnerability management, and compliance management, making them an ideal solution for organizations navigating digital transformation in various industries, including banking, industrial, and consumer data protection.
Cloud security solutions, such as Lacework and Orca Security, offer runtime security, monitoring, logging, and artificial intelligence (AI) and machine learning (ML) capabilities to protect cloud environments from cyber threats, including malicious intrusions, malware, and ransomware attacks. The consolidation of security companies and the increasing focus on IT operation efficiency further drive the demand for cloud workload protection solutions.
Get a glance at the Cloud Workload Protection Industry report of share of various segments Request Free Sample
The Hybrid segment was valued at USD 598.20 billion in 2018 and showed a gradual increase during the forecast period.
Regional Analysis
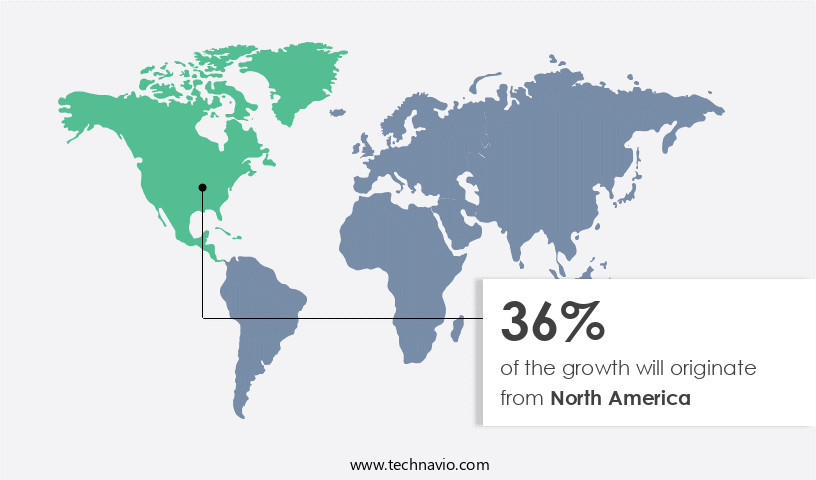
- North America is estimated to contribute 36% to the growth of the global market during the forecast period.
Technavio’s analysts have elaborately explained the regional trends and drivers that shape the market during the forecast period.
For more insights on the market share of various regions, Request Free Sample
The market is a significant segment of the cybersecurity industry, focusing on securing workloads in various cloud environments, including multi-cloud networks, hybrid IT, and on-premises servers. In 2023, North America led the market due to advanced economies, a strong focus on innovation, and a diverse technology landscape. Canada, in particular, is a key market due to its technological advances, early adoption of modern technologies, and the presence of numerous SMEs. The country's industrial and private sectors are witnessing significant growth, leading to increased interest in cloud platforms and the adoption of cloud security solutions. Threats such as malicious intrusions, malware, and unpatched vulnerabilities continue to pose risks to cloud environments, making robust security controls essential.
Cybersecurity solutions for cloud workloads include threat detection, vulnerability management, compliance management, runtime security, monitoring, logging, and artificial intelligence (AI) and machine learning (ML) technologies for enhanced security posture and custom security policies. As businesses continue their digital transformation journey, the demand for cloud security solutions will persist, with large enterprises under increased cybersecurity scrutiny. The market is expected to grow as organizations seek to protect their cloud VMs, serverless workloads, and containers from cyber threats such as ransomware attacks and unauthorized network access.
Market Dynamics
Our researchers analyzed the data with 2023 as the base year, along with the key drivers, trends, and challenges. A holistic analysis of drivers will help companies refine their marketing strategies to gain a competitive advantage.
What are the key market drivers leading to the rise In the adoption of Cloud Workload Protection Industry?
Increasing cases of cybersecurity attacks is the key driver of the market.
What are the market trends shaping the Cloud Workload Protection Industry?
Increasing adoption of cloud workload protection in BFSI sector is the upcoming market trend.
What challenges does the Cloud Workload Protection Industry face during its growth?
Lack of technical expertise in developing countries is a key challenge affecting the industry growth.
Exclusive Customer Landscape
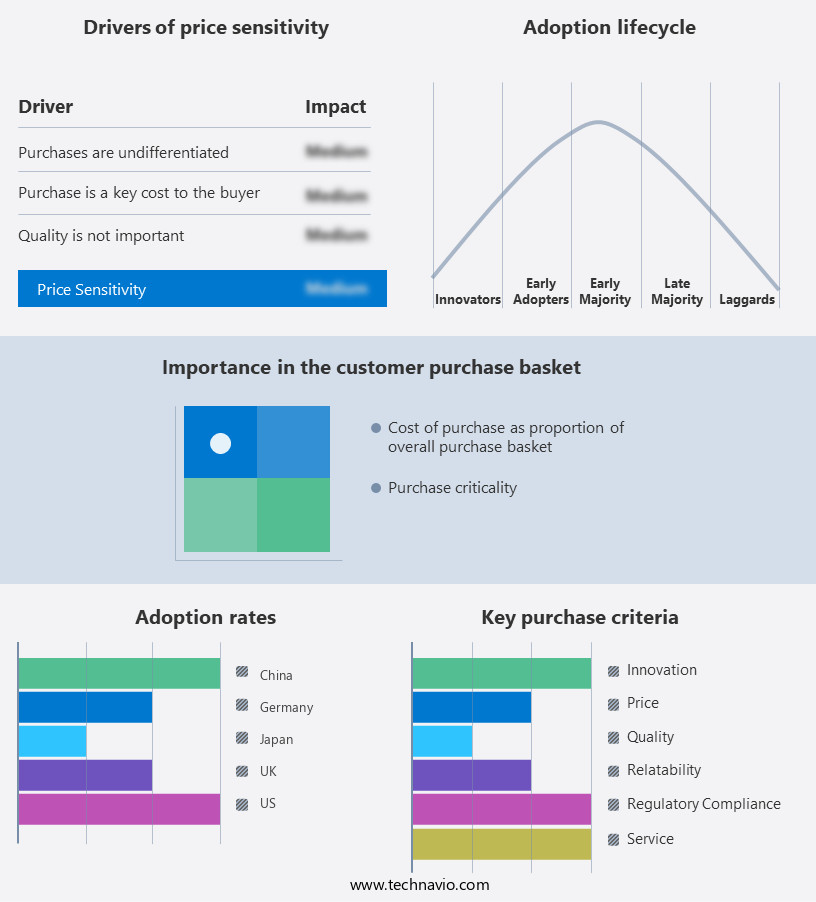
The cloud workload protection market forecasting report includes the adoption lifecycle of the market, covering from the innovator’s stage to the laggard’s stage. It focuses on adoption rates in different regions based on penetration. Furthermore, the cloud workload protection market report also includes key purchase criteria and drivers of price sensitivity to help companies evaluate and develop their market growth analysis strategies.
Customer Landscape
Key Companies & Market Insights
Companies are implementing various strategies, such as strategic alliances, cloud workload protection market forecast, partnerships, mergers and acquisitions, geographical expansion, and product/service launches, to enhance their presence In the industry.
Akamai Technologies Inc. - The market for cloud workload protection provides businesses with agility through cloud-native security solutions that seamlessly integrate with DevOps and continuous integration/continuous delivery (CI/CD) pipelines. These offerings ensure the security and compliance of cloud-based applications and infrastructure, enabling organizations to effectively manage risk and maintain operational efficiency. By implementing cloud workload protection, businesses can secure their workloads against advanced threats, maintain regulatory compliance, and accelerate their digital transformation initiatives.
The industry research and growth report includes detailed analyses of the competitive landscape of the market and information about key companies, including:
- Akamai Technologies Inc.
- Alphabet Inc.
- AO Kaspersky Lab
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- CloudPassage Inc.
- ColorTokens Inc.
- Entrust Corp.
- Guardicore Ltd.
- LogRhythm Inc.
- McAfee LLC
- Microsoft Corp.
- Nutanix Inc.
- Orca Security Ltd.Ã
- Palo Alto Networks Inc.
- Qualys Inc.
- Sophos Ltd.
- StackRox Inc.
- Sysdig Inc.
- Trend Micro Inc.
Qualitative and quantitative analysis of companies has been conducted to help clients understand the wider business environment as well as the strengths and weaknesses of key industry players. Data is qualitatively analyzed to categorize companies as pure play, category-focused, industry-focused, and diversified; it is quantitatively analyzed to categorize companies as dominant, leading, strong, tentative, and weak.
Research Analyst Overview
Cloud workload protection has emerged as a critical aspect of IT security In the current digital landscape, particularly as businesses increasingly adopt multi-cloud infrastructure to support their digital transformation initiatives. This shift towards multi-cloud environments has introduced new complexities and challenges for IT teams, requiring them to implement robust security measures to protect their cloud workloads from various cyber threats. Multi-cloud infrastructure refers to the use of multiple cloud platforms, including public, private, and hybrid clouds, to meet the diverse needs of modern businesses. This approach offers numerous benefits, such as increased flexibility, scalability, and cost savings. However, it also introduces new security complexities, as each cloud environment requires unique security configurations and management.
Security is a top concern for organizations across industries, including banking, industrial, and consumer sectors. With the increasing sophistication of cyber attacks, traditional security approaches are no longer sufficient to protect against malicious intrusions, malware, and other cyber threats. Cloud workload protection solutions have gained popularity due to their ability to provide centralized data protection and threat detection capabilities for cloud environments. DevOps teams play a crucial role In the implementation and management of cloud workloads. They are responsible for automating the deployment, scaling, and management of applications and infrastructure in cloud environments. However, their focus on agility and speed can sometimes lead to security oversights, leaving cloud workloads vulnerable to cyber threats.
Hybrid IT environments, which combine on-premises servers and cloud infrastructure, present additional challenges for IT teams. They must ensure that their security controls are consistent across both environments to maintain a strong security posture. Containers and virtual machines (VMs) are common components of hybrid IT environments and require specialized security solutions to protect against vulnerabilities and compliance risks. Serverless workloads, which run In the cloud without the need for a dedicated server, have also gained popularity due to their cost-effectiveness and scalability. However, they introduce new security challenges, as they are often difficult to secure due to their ephemeral nature and dynamic runtime environment.
Vulnerability management and compliance management are essential components of cloud workload protection. IT teams must ensure that their cloud environments are compliant with industry regulations and best practices to mitigate risks and avoid costly breaches. Runtime security solutions and monitoring and logging capabilities are critical for identifying and responding to threats in real-time. Cybersecurity scrutiny is at an all-time high, with regulatory bodies and consumers demanding greater transparency and accountability from organizations regarding their data privacy and security practices. Cloud platforms and security solution providers are responding to this trend by offering advanced security features and services to help businesses protect their cloud workloads and maintain a strong security posture.
The consolidation of security companies is another trend In the market. Large enterprises are increasingly looking for comprehensive security solutions that can provide protection across their entire IT infrastructure, including their cloud environments. Consulting and integration services are also becoming more important as businesses seek to optimize their IT operations and improve their security posture. In conclusion, cloud workload protection is a critical aspect of IT security In the digital age, particularly as businesses adopt multi-cloud infrastructure to support their digital transformation initiatives. IT teams must implement robust security measures to protect their cloud workloads from various cyber threats and maintain a strong security posture.
This requires a multi-faceted approach that includes vulnerability management, compliance management, runtime security, monitoring, and logging capabilities. Cloud platforms and security solution providers are responding to this trend by offering advanced security features and services to help businesses protect their cloud workloads and maintain compliance with industry regulations and best practices.
|
Market Scope |
|
|
Report Coverage |
Details |
|
Page number |
136 |
|
Base year |
2023 |
|
Historic period |
2018-2022 |
|
Forecast period |
2024-2028 |
|
Growth momentum & CAGR |
Accelerate at a CAGR of 26.1% |
|
Market growth 2024-2028 |
USD 5504.1 million |
|
Market structure |
Fragmented |
|
YoY growth 2023-2024(%) |
21.6 |
|
Key countries |
US, China, UK, Germany, and Japan |
|
Competitive landscape |
Leading Companies, Market Positioning of Companies, Competitive Strategies, and Industry Risks |
What are the Key Data Covered in this Cloud Workload Protection Market Research and Growth Report?
- CAGR of the Cloud Workload Protection industry during the forecast period
- Detailed information on factors that will drive the growth and forecasting between 2024 and 2028
- Precise estimation of the size of the market and its contribution of the industry in focus to the parent market
- Accurate predictions about upcoming growth and trends and changes in consumer behaviour
- Growth of the market across North America, Europe, APAC, Middle East and Africa, and South America
- Thorough analysis of the market’s competitive landscape and detailed information about companies
- Comprehensive analysis of factors that will challenge the cloud workload protection market growth of industry companies
We can help! Our analysts can customize this cloud workload protection market research report to meet your requirements.