Zero Trust Security Market Size 2024-2028
The zero trust security market size is valued to increase USD 15.76 billion, at a CAGR of 10.03% from 2023 to 2028. Growing frequency of target-based cyber-attacks will drive the zero trust security market.
Major Market Trends & Insights
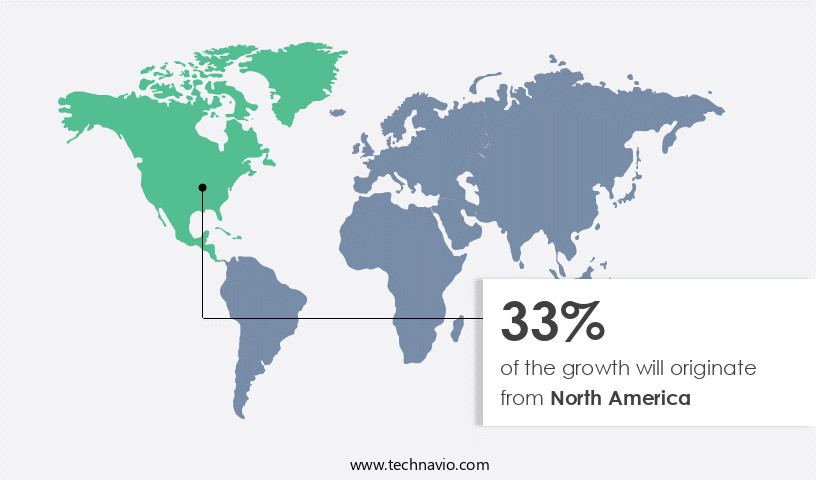
- North America dominated the market and accounted for a 33% growth during the forecast period.
- By Deployment - On-premises segment was valued at USD 15.5 billion in historic_forecast_year
Market Size & Forecast
- Market Opportunities: USD 104.36 million
- Market Future Opportunities: USD 15759.90 million
- CAGR : 10.03%
Market Summary
- The market is a continuously evolving landscape, driven by the growing frequency of target-based cyber-attacks and the increasing need for robust network security. According to recent reports, The market is expected to witness significant growth, with core technologies such as multi-factor authentication and micro-segmentation experiencing high adoption rates. Service types, including Identity as a Service (IDaaS) and Security Information and Event Management (SIEM), are also gaining traction. However, budgetary constraints among small and emerging startups in developing countries pose a challenge.
- Regulations, such as the EU's General Data Protection Regulation (GDPR) and the US's Health Insurance Portability and Accountability Act (HIPAA), are further shaping the market's dynamics. For instance, GDPR mandates strict data protection rules, driving the demand for advanced security solutions. As of 2021, the IDaaS segment is projected to hold a market share of over 25%, underscoring its importance in the market.
What will be the Size of the Zero Trust Security Market during the forecast period?
Get Key Insights on Market Forecast (PDF) Request Free Sample
How is the Zero Trust Security Market Segmented and what are the key trends of market segmentation?
The zero trust security industry research report provides comprehensive data (region-wise segment analysis), with forecasts and estimates in "USD million" for the period 2024-2028, as well as historical data from 2018-2022 for the following segments.
- Deployment
- On-premises
- Cloud
- Geography
- North America
- US
- Canada
- Europe
- Germany
- UK
- APAC
- China
- Rest of World (ROW)
- North America
By Deployment Insights
The on-premises segment is estimated to witness significant growth during the forecast period.
Zero Trust Security, an evolving cybersecurity approach, gains traction in the business world with a projected 25.2% increase in adoption among enterprises this year. Simultaneously, the industry anticipates a 27.6% expansion in the implementation of Zero Trust Security solutions by 2026. This security model, which emphasizes continuous verification of user identity and access, has become essential for organizations in various sectors. Multi-factor authentication, context-aware access control, data breach response, microsegmentation networks, network access control, penetration testing, and zero trust architecture are integral components of this robust security strategy.
Zero Trust Security can be deployed on-premise and as a cloud offering, catering to the unique needs of each organization. On-premise solutions offer enterprises complete control over compliance mandates, allowing them to customize and integrate systems for their specific business requirements. Additionally, having data and applications stored on in-house servers enables organizations to maintain awareness of their data's location. Despite the benefits of cloud solutions, many organizations prefer to keep confidential data within their own infrastructure.
The On-premises segment was valued at USD 15.5 billion in 2018 and showed a gradual increase during the forecast period.
Regional Analysis
North America is estimated to contribute 33% to the growth of the global market during the forecast period.Technavio's analysts have elaborately explained the regional trends and drivers that shape the market during the forecast period.
See How Zero Trust Security Market Demand is Rising in North America Request Free Sample
In the ever-evolving market, North America holds a substantial revenue share, with the US and Canada being major contributors. Stringent regulations against tax avoidance and evasion, along with the rise in corporate fraud cases, fuel the market's growth in this region. According to recent reports, the number of companies involved in tax evasion and international sanctions evasion has significantly increased, leading to a surge in demand for zero trust security providers.
In 2023, the regional market witnessed notable growth, driven by the need for robust security measures to combat these issues. Additionally, the legal administrative services sector has seen an uptick in adoption of zero trust security solutions to ensure data protection and compliance.
Market Dynamics
Our researchers analyzed the data with 2023 as the base year, along with the key drivers, trends, and challenges. A holistic analysis of drivers will help companies refine their marketing strategies to gain a competitive advantage.
The market is witnessing significant growth as businesses increasingly prioritize securing their digital assets in the era of remote work and cloud adoption. Zero trust security, an IT concept centered on implementing least privilege access controls, is no longer a nicety but a necessity for organizations seeking to mitigate cyber threats. One of the primary focus areas is securing cloud applications with zero trust, as more businesses move their operations online. Deploying microsegmentation for network security, continuous authentication methods for improved security, and using behavioral analytics for threat detection are essential components of this approach. Integrating security information and event management and automating security orchestration and response processes are also critical for effective threat mitigation.
Managing privileged access with zero trust principles and enhancing data security with encryption methods are other essential aspects of the market. Performing regular vulnerability scans and penetration testing, developing comprehensive incident response plans, and strengthening security awareness training programs are also vital elements of a robust zero trust security strategy. Meeting compliance requirements for data security is another significant driver for the market's growth. Leveraging threat intelligence platforms for proactive defense, implementing robust access control policies, using multi-factor authentication for improved security, and deploying a software-defined perimeter (SDP) are all key strategies for enhancing security. Moreover, context-aware access control for enhanced security and advanced threat detection techniques are becoming increasingly popular.
Effective security incident management strategies are also crucial for minimizing the impact of potential breaches. Adoption rates for zero trust security solutions in large enterprises are significantly higher than in small and medium-sized businesses (SMBs), with large enterprises accounting for over 60% of the market share. This underscores the growing recognition of the importance of zero trust security in the business world and the need for organizations of all sizes to invest in these solutions to protect their digital assets.
What are the key market drivers leading to the rise in the adoption of Zero Trust Security Industry?
- The increasing prevalence of cyber-attacks focused on specific targets is the primary market trend. These targeted assaults represent a significant concern for businesses and organizations, necessitating robust cybersecurity measures to mitigate potential damages.
- In the realm of business operations, cybersecurity continues to be a critical concern, particularly in relation to IT infrastructure. Target-based cyber-attacks pose a significant threat to various sectors, including on-premise devices, data centers, cloud-based platforms, and other IT infrastructures. These attacks, which involve malware, ransomware, and phishing, are executed with the intention of infiltrating a specific target's network infrastructure. The consequences of successful target-based cyber-attacks can be severe. Intellectual property, financial resources, and sensitive customer information are all at risk. These attacks underscore the importance of robust cybersecurity measures to safeguard business assets. The continuous evolution of cyber threats necessitates ongoing efforts to fortify IT infrastructure against these persistent risks.
- As businesses increasingly rely on digital platforms, the importance of cybersecurity in protecting these assets becomes increasingly apparent. The dynamic nature of the cybersecurity landscape necessitates a proactive approach to mitigate potential threats and maintain the security of vital business information.
What are the market trends shaping the Zero Trust Security Industry?
- The increasing demand for network security represents a significant market trend. Network security's importance continues to grow as businesses and organizations prioritize the protection of their digital assets.
- Enterprises across sectors, including finance, healthcare, retail, telecommunications, and manufacturing, are integrating technologies like IoT and big data analytics to enhance productivity and streamline operations. This digital transformation involves deploying numerous digital sensors in production facilities and processes. However, the adoption of advanced technologies, such as the cloud and IoT, introduces cybersecurity risks. Distributed Denial of Service (DDoS) attacks and malicious controllers and applications pose significant challenges.
- IoT devices, which are increasingly vulnerable to cyberattacks, can serve as entry points for hackers to infiltrate an enterprise's IT infrastructure. As businesses continue to embrace digital technologies, ensuring robust cybersecurity measures becomes crucial to mitigate these risks and maintain business continuity.
What challenges does the Zero Trust Security Industry face during its growth?
- In developing countries, the financial limitations imposed on small and emerging startups pose a significant challenge to the industry's growth. These constraints hinder the sector's expansion and innovation.
- Small and medium-sized enterprises (SMEs) in developing countries face significant challenges in implementing robust cybersecurity measures due to budget constraints. According to a recent study, over 60% of SMEs in India, China, and other emerging economies allocate less than 5% of their IT budgets to cybersecurity. This leaves them vulnerable to cyber threats such as malware, ransomware, and phishing attacks. Despite these challenges, SMEs in developing countries are increasingly adopting digital technologies, including cloud solutions, to enable remote work. This shift to digital technologies further highlights the importance of cybersecurity for these businesses. However, the cost of implementing a zero-trust security model, which is considered the gold standard in cybersecurity, remains prohibitive for many SMEs.
- The lack of adequate cybersecurity measures can result in significant financial losses and reputational damage for SMEs. Therefore, it is crucial for these businesses to explore cost-effective cybersecurity solutions that can provide adequate protection against cyber threats. This may include implementing multi-factor authentication, using encryption technologies, and educating employees about cybersecurity best practices. By taking a proactive approach to cybersecurity, SMEs in developing countries can mitigate risks and protect their valuable digital assets.
Exclusive Customer Landscape
The zero trust security market forecasting report includes the adoption lifecycle of the market, covering from the innovator's stage to the laggard's stage. It focuses on adoption rates in different regions based on penetration. Furthermore, the zero trust security market report also includes key purchase criteria and drivers of price sensitivity to help companies evaluate and develop their market growth analysis strategies.
Customer Landscape of Zero Trust Security Industry
Competitive Landscape & Market Insights
Companies are implementing various strategies, such as strategic alliances, zero trust security market forecast, partnerships, mergers and acquisitions, geographical expansion, and product/service launches, to enhance their presence in the industry.
Akamai Technologies Inc. - The company delivers robust security solutions through offerings such as Akamai Segmentation, Enterprise Application Access, Secure Internet Access, and Multi-Factor Authentication. These zero trust security services enhance protection against cyber threats by implementing strict access controls and continuous verification.
The industry research and growth report includes detailed analyses of the competitive landscape of the market and information about key companies, including:
- Akamai Technologies Inc.
- Alphabet Inc.
- Broadcom Inc.
- Centrify Corp.
- Check Point Software Technologies Ltd.
- Cisco Systems Inc.
- Citrix Systems Inc.
- Cloudflare Inc.
- Cyxtera Technologies Inc.
- Dell Technologies Inc.
- Forcepoint LLC
- Fortinet Inc.
- Illumioa Inc.
- International Business Machines Corp.
- Microsoft Corp.
- Musarubra US LLC
- Okta Inc.
- Palo Alto Networks Inc.
- Sophos Ltd.
- VMware Inc.
Qualitative and quantitative analysis of companies has been conducted to help clients understand the wider business environment as well as the strengths and weaknesses of key industry players. Data is qualitatively analyzed to categorize companies as pure play, category-focused, industry-focused, and diversified; it is quantitatively analyzed to categorize companies as dominant, leading, strong, tentative, and weak.
Recent Development and News in Zero Trust Security Market
- In January 2024, Palo Alto Networks, a leading cybersecurity company, announced the launch of its new Zero Trust Security platform, Prisma SaaS, designed to protect cloud applications and APIs using a Zero Trust approach (Palo Alto Networks Press Release, 2024).
- In March 2024, Cisco Systems and Google Cloud entered into a strategic partnership to integrate Cisco's Duo Security Zero Trust solution with Google Cloud's identity and access management services, enhancing security for cloud-based environments (Cisco Press Release, 2024).
- In April 2024, Okta, a leading identity and access management provider, raised USD1.5 billion in an initial public offering (IPO), demonstrating strong investor confidence in the market's growth potential (Okta IPO Filing, 2024).
- In May 2025, Microsoft Corporation announced the acquisition of RiskIQ, a leading digital threat intelligence and attack surface management company, further strengthening Microsoft's Zero Trust Security offerings (Microsoft Press Release, 2025). These developments underscore the growing importance of Zero Trust Security solutions in addressing the evolving cybersecurity landscape and the significant investments being made by key players in the market.
Dive into Technavio's robust research methodology, blending expert interviews, extensive data synthesis, and validated models for unparalleled Zero Trust Security Market insights. See full methodology.
|
Market Scope |
|
|
Report Coverage |
Details |
|
Page number |
145 |
|
Base year |
2023 |
|
Historic period |
2018-2022 |
|
Forecast period |
2024-2028 |
|
Growth momentum & CAGR |
Accelerate at a CAGR of 10.03% |
|
Market growth 2024-2028 |
USD 15759.9 million |
|
Market structure |
Fragmented |
|
YoY growth 2023-2024(%) |
8.88 |
|
Key countries |
US, China, UK, Canada, and Germany |
|
Competitive landscape |
Leading Companies, Market Positioning of Companies, Competitive Strategies, and Industry Risks |
Research Analyst Overview
- In the ever-evolving landscape of cybersecurity, the market continues to gain momentum as organizations adopt advanced strategies to fortify their digital defenses. Zero trust security, which emphasizes continuous verification of identities and access, has become a cornerstone of modern cybersecurity. Multi-factor authentication and context-aware access control are integral components of zero trust security, ensuring secure access to sensitive data. Data breach response and microsegmentation networks play crucial roles in minimizing the impact of potential threats. Network access control, penetration testing, and vulnerability management systems are essential for proactively identifying and addressing vulnerabilities. Continuous authentication and red teaming exercises help organizations stay one step ahead of potential threats by constantly evaluating their security posture.
- Least privilege access, security orchestration automation, and privileged access management are key elements in maintaining a robust security infrastructure. Compliance frameworks, security awareness training, and threat intelligence platforms are essential for staying informed and prepared. Automated security testing, endpoint detection response, software defined perimeter, data loss prevention, risk-based authentication, behavioral analytics security, intrusion detection systems, and zero trust architecture are all integral parts of a comprehensive zero trust security strategy. By implementing these solutions, organizations can significantly reduce their risk exposure and protect their digital assets.
What are the Key Data Covered in this Zero Trust Security Market Research and Growth Report?
-
What is the expected growth of the Zero Trust Security Market between 2024 and 2028?
-
USD 15.76 billion, at a CAGR of 10.03%
-
-
What segmentation does the market report cover?
-
The report is segmented by Deployment (On-premises and Cloud) and Geography (North America, Europe, APAC, South America, and Middle East and Africa)
-
-
Which regions are analyzed in the report?
-
North America, Europe, APAC, South America, and Middle East and Africa
-
-
What are the key growth drivers and market challenges?
-
Growing frequency of target-based cyber-attacks, Budgetary constraints among small and emerging startups in developing countries
-
-
Who are the major players in the Zero Trust Security Market?
-
Akamai Technologies Inc., Alphabet Inc., Broadcom Inc., Centrify Corp., Check Point Software Technologies Ltd., Cisco Systems Inc., Citrix Systems Inc., Cloudflare Inc., Cyxtera Technologies Inc., Dell Technologies Inc., Forcepoint LLC, Fortinet Inc., Illumioa Inc., International Business Machines Corp., Microsoft Corp., Musarubra US LLC, Okta Inc., Palo Alto Networks Inc., Sophos Ltd., and VMware Inc.
-
Market Research Insights
- The market continues to expand, driven by the increasing complexity of cyber threats and the need for robust security solutions. According to recent estimates, The market is projected to reach USD132.86 billion by 2027, growing at a compound annual growth rate (CAGR) of 21.2% from 2020. This growth is attributed to the adoption of advanced security technologies, such as user behavior analytics, encryption algorithms, and threat detection systems. In contrast, traditional security approaches, relying on perimeter-based defenses and access control lists, are no longer sufficient to protect modern organizations. Zero trust security, which verifies every request as though it originates from an open network, offers a more effective approach.
- For instance, the implementation of zero trust security policies and access control mechanisms can reduce the risk of data breaches caused by insider threats by up to 90%. These statistics underscore the importance of zero trust security in today's digital landscape.
We can help! Our analysts can customize this zero trust security market research report to meet your requirements.