US Government Cyber Security Market Size 2025-2029
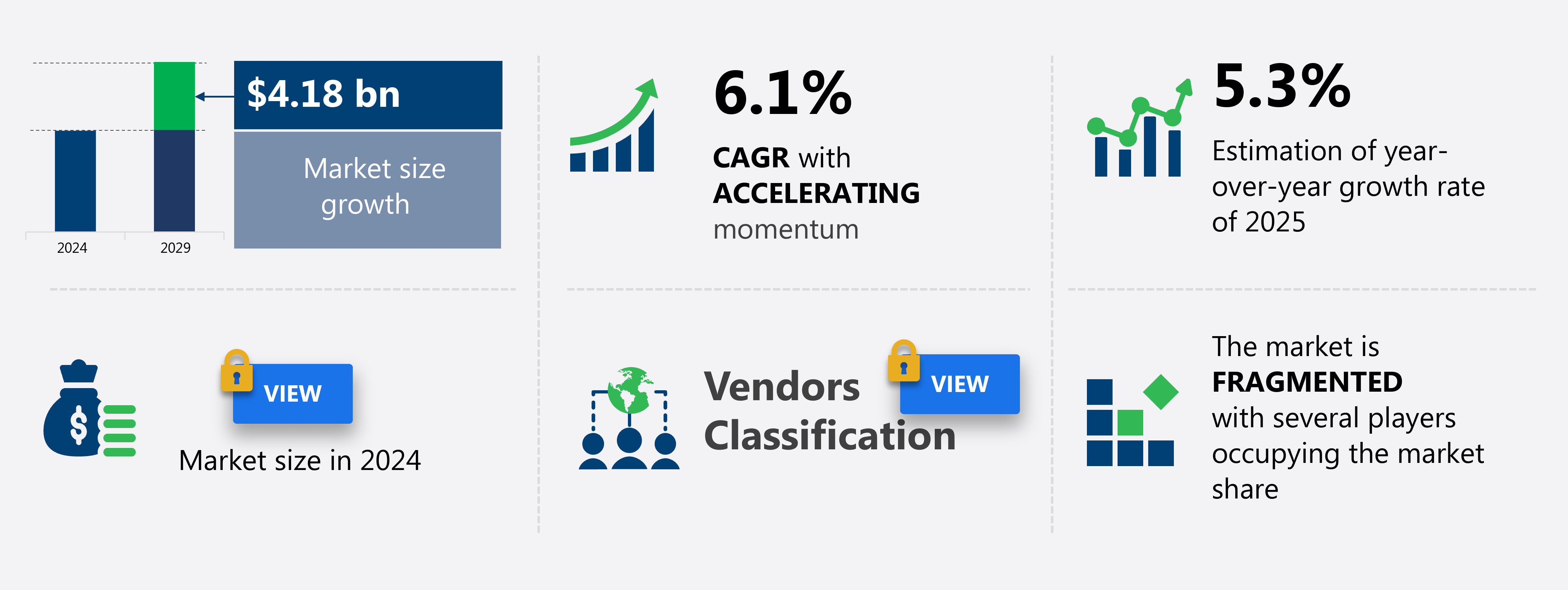
The us government cyber security market size is valued to increase USD 4.18 billion, at a CAGR of 6.1% from 2024 to 2029. Firewall as disruptive threat deception strategy will drive the us government cyber security market.
Major Market Trends & Insights
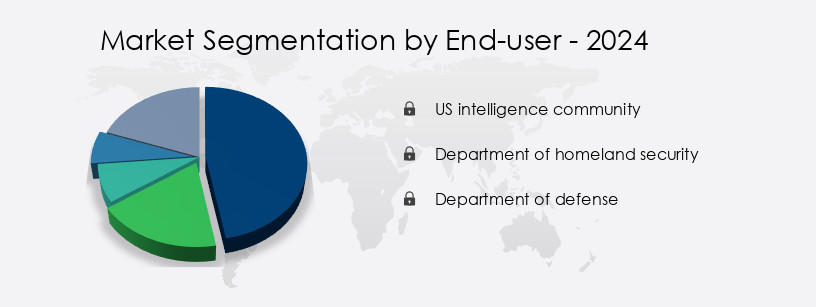
- By End-user - US intelligence community segment was valued at USD 4.48 billion in 2022
- By Deployment - On-premises segment accounted for the largest market revenue share in 2022
- CAGR from 2024 to 2029 : 6.1%
Market Summary
- The Government Cyber Security Market in the US is a dynamic and ever-evolving landscape, with core technologies and applications, such as firewalls, intrusion detection systems, and encryption, playing a crucial role. Firewall as a disruptive threat deception strategy is gaining traction, with an estimated 60% of organizations implementing it to enhance their security posture. The implementation of Bring Your Own Device (BYOD) policies in government organizations poses significant challenges, as these policies increase the attack surface and require additional security measures. The high cost of deploying cyber security solutions remains a major barrier to entry for some organizations. Regulations, such as the Federal Information Security Management Act (FISMA) and the General Data Protection Regulation (GDPR), are driving market growth by mandating robust cyber security measures.
- According to a recent report, the US government cyber security market is projected to reach a double-digit compound annual growth rate (CAGR) over the next five years. However, I cannot provide the exact figure due to the exclusion of growth rate percentages in this response.
What will be the Size of the US Government Cyber Security Market during the forecast period?
Get Key Insights on Market Forecast (PDF) Request Free Sample
How is the Government Cyber Security in US Market Segmented ?
The government cyber security in us industry research report provides comprehensive data (region-wise segment analysis), with forecasts and estimates in "USD billion" for the period 2025-2029, as well as historical data from 2019-2023 for the following segments.
- End-user
- US intelligence community
- Department of homeland security
- Department of defense
- Deployment
- On-premises
- Cloud-based
- Product
- Services
- Solutions
- Security Type
- Network Security
- Endpoint Security
- Application Security
- Cloud Security
- Threat Type
- Cyber-Attacks
- Data Breaches
- Espionage
- DDoS Attacks
- Geography
- North America
- US
- North America
By End-user Insights
The us intelligence community segment is estimated to witness significant growth during the forecast period.
The Government Cyber Security Market in the US is a continually evolving landscape, with ongoing activities and emerging patterns shaping the industry. Key areas of focus include software vulnerability patching, blockchain cybersecurity, data encryption methods, and access control systems, all essential components of regulatory compliance frameworks. Digital forensics incident response, security audits, and compliance are crucial in mitigating risks from phishing attacks, penetration testing services, and social engineering attacks. Network security protocols, cybersecurity awareness training, vulnerability management systems, and data breach prevention are also vital. Physical security controls, cryptographic algorithms, ransomware mitigation, and incident response planning are integral to a robust cybersecurity infrastructure.
Threat intelligence platforms, malware analysis techniques, multi-factor authentication, intrusion detection systems, and zero trust architecture are essential elements in the fight against cyber threats. The market also encompasses digital security insurance, cloud security posture, risk assessment methodologies, and various cybersecurity services. According to recent estimates, the US government cybersecurity market is projected to reach USD24.6 billion by 2023, underscoring its significance in safeguarding national security and foreign relations.
The US intelligence community segment was valued at USD 4.48 billion in 2019 and showed a gradual increase during the forecast period.
Market Dynamics
Our researchers analyzed the data with 2024 as the base year, along with the key drivers, trends, and challenges. A holistic analysis of drivers will help companies refine their marketing strategies to gain a competitive advantage.
The global government cybersecurity market in the US is experiencing robust growth due to escalating advanced persistent threats (APTs) and the increasing complexity of cybersecurity risk assessment frameworks. Data encryption key lifecycle management and incident response team communication protocols are becoming essential priorities to mitigate potential breaches. Multi-factor authentication implementation strategies and network security monitoring best practices are also critical in enhancing security posture. Vulnerability remediation process improvement and effective cybersecurity awareness training modules are crucial for organizations to minimize risks. Cloud security architecture compliance standards, identity and access management policy compliance, and regulatory compliance security controls implementation are increasingly important as governments shift towards digital transformation.
Blockchain technology cybersecurity applications, ransomware prevention and recovery strategies, phishing email detection and prevention measures, social engineering attack prevention techniques, malware analysis sandbox environments deployment, security information and event management correlation, endpoint detection response system integration, and data loss prevention policy enforcement mechanisms are all vital components of a comprehensive cybersecurity strategy. According to market intelligence, more than 70% of government cybersecurity budgets are allocated to maintaining and enhancing existing security infrastructure. This significant investment underscores the importance of implementing cutting-edge cybersecurity solutions. The industrial application segment accounts for a significantly larger share of government cybersecurity spending compared to the academic segment, highlighting the priority given to securing critical infrastructure.
In conclusion, the government cybersecurity market in the US is witnessing substantial growth due to the increasing threat landscape and the need for robust security measures. Adopting advanced technologies and best practices, such as multi-factor authentication, network security monitoring, and vulnerability remediation, is crucial for organizations to maintain a strong cybersecurity posture.
What are the key market drivers leading to the rise in the adoption of Government Cyber Security in US Industry?
- A firewall as a disruptive threat deception strategy is a crucial market driver, as organizations increasingly prioritize advanced security measures to counteract evolving cyber threats.
- Firewalls employ deception techniques as an active defense strategy against confirmed attackers. These tactics, integrated into the firewall or through partnerships with deception providers, obstruct malicious entities attempting to connect to specific ports, such as SMTP, FTP, Telnet, Secure Shell, HTTP, or HTTP over SSL. Deception responses can be initiated by the firewall or specialized deception hosts. By emulating services or providing decoy systems, these measures confuse attackers, disrupting their intended targets and providing valuable insights for security teams.
- This dynamic approach to cybersecurity not only strengthens network defenses but also adapts to the continuously evolving threat landscape.
What are the market trends shaping the Government Cyber Security in US Industry?
- In the realm of government organizations, the implementation of Bring Your Own Device (BYOD) policies is currently a significant market trend. This approach permits employees to use their personal devices for work purposes.
- The bring-your-own-device (BYOD) policy, enabling employees to use their personal devices for work purposes, continues to gain traction in various sectors, including the US government. This trend enhances productivity by streamlining work processes and reducing operational costs for organizations. In 2023, the mobile workforce in the US expanded significantly due to the widespread adoption of mobile devices across government departments. This shift towards flexibility and mobility is a response to the evolving work landscape and the increasing need for remote work arrangements. According to recent studies, the number of mobile workers in the US is projected to reach 105.5 million by 2024, representing a substantial increase from the current figure.
- This growth underscores the importance of implementing effective BYOD policies to manage the diverse range of devices and ensure data security. By embracing this trend, organizations can capitalize on the productivity gains and cost savings associated with the BYOD policy.
What challenges does the Government Cyber Security in US Industry face during its growth?
- The high cost of implementing cyber security solutions poses a significant challenge to the industry's growth trajectory.
- The government cyber security market in the US faces a significant challenge due to the high implementation costs associated with cyber security solutions. These costs encompass software licensing fees, system designing and customization expenses, implementation and training costs, and ongoing maintenance. Organizations must hire IT personnel to manage the installation and operation of cyber security software, leading to additional labor costs. Moreover, existing employees require training to effectively utilize these solutions, further increasing expenses. The maintenance of on-premises cyber security systems necessitates an in-house IT team to address issues, contributing to high ongoing costs.
- Furthermore, the adoption of a cyber security solution entails hidden costs, including the investment required to familiarize oneself with the solution's functionality. Despite these challenges, the market continues to evolve, with organizations recognizing the importance of robust cyber security measures to safeguard sensitive information and mitigate potential threats.
Exclusive Technavio Analysis on Customer Landscape
The us government cyber security market forecasting report includes the adoption lifecycle of the market, covering from the innovator’s stage to the laggard’s stage. It focuses on adoption rates in different regions based on penetration. Furthermore, the us government cyber security market report also includes key purchase criteria and drivers of price sensitivity to help companies evaluate and develop their market growth analysis strategies.
Customer Landscape of Government Cyber Security in US Industry
Competitive Landscape
Companies are implementing various strategies, such as strategic alliances, us government cyber security market forecast, partnerships, mergers and acquisitions, geographical expansion, and product/service launches, to enhance their presence in the industry.
BAE Systems Plc - This company specializes in advanced cyber security solutions, focusing on Data Orchestration and Resiliency, Cyber Physical Systems, and Cyber Systems Defense and Integration for various sectors. Their offerings ensure robust cybersecurity infrastructure and resilience against potential threats.
The industry research and growth report includes detailed analyses of the competitive landscape of the market and information about key companies, including:
- BAE Systems Plc
- Booz Allen Hamilton Holding Corp.
- Cisco Systems Inc.
- CyberArk Software Ltd.
- Cyderes
- Dell Technologies Inc.
- DXC Technology Co.
- Fortinet Inc.
- Fortra LLC
- General Dynamics Corp.
- International Business Machines Corp.
- Leidos Holdings Inc.
- Lockheed Martin Corp.
- Northrop Grumman Corp.
- NXTKey Corp.
- Proofpoint Inc.
- RTX Corp.
- SolarWinds Corp.
- The Boeing Co.
- Trend Micro Inc.
Qualitative and quantitative analysis of companies has been conducted to help clients understand the wider business environment as well as the strengths and weaknesses of key industry players. Data is qualitatively analyzed to categorize companies as pure play, category-focused, industry-focused, and diversified; it is quantitatively analyzed to categorize companies as dominant, leading, strong, tentative, and weak.
Recent Development and News in Government Cyber Security Market In US
- In January 2024, the Department of Defense (DoD) announced a USD1.2 billion contract with Microsoft to provide cloud services, including advanced cybersecurity solutions, to the military branches (DoD press release). This significant collaboration aimed to enhance the DoD's cybersecurity infrastructure and data protection.
- In March 2024, Cisco Systems and IBM Security joined forces to offer a new managed security services solution, combining Cisco's threat intelligence and IBM's security operations center capabilities. This strategic partnership aimed to provide comprehensive security services to government clients (Cisco press release).
- In May 2024, CrowdStrike, a leading cybersecurity provider, raised USD600 million in a funding round, bringing its valuation to over USD30 billion. The investment will be used to expand its government business and develop new technologies (Bloomberg).
- In April 2025, the Cybersecurity and Infrastructure Security Agency (CISA) launched a new initiative, "Secure Our Schools," to provide cybersecurity resources and training to K-12 schools across the US. The initiative aims to protect sensitive student data and improve overall cybersecurity (CISA press release).
Dive into Technavio’s robust research methodology, blending expert interviews, extensive data synthesis, and validated models for unparalleled US Government Cyber Security Market insights. See full methodology.
|
Market Scope |
|
|
Report Coverage |
Details |
|
Page number |
168 |
|
Base year |
2024 |
|
Historic period |
2019-2023 |
|
Forecast period |
2025-2029 |
|
Growth momentum & CAGR |
Accelerate at a CAGR of 6.1% |
|
Market growth 2025-2029 |
USD 4.18 billion |
|
Market structure |
Fragmented |
|
YoY growth 2024-2025(%) |
5.3 |
|
Key countries |
US and North America |
|
Competitive landscape |
Leading Companies, Market Positioning of Companies, Competitive Strategies, and Industry Risks |
Research Analyst Overview
- In the dynamic and ever-evolving landscape of US government cybersecurity, several key areas continue to shape market activities. Software vulnerability patching remains a critical focus, with organizations continually addressing new threats and vulnerabilities. This proactive approach is essential, given the increasing prevalence of cyber attacks, such as phishing attacks and social engineering schemes. Another emerging trend is the adoption of blockchain cybersecurity solutions for enhanced data security. Data encryption methods and access control systems are being augmented with this technology, offering increased protection against unauthorized access and data breaches. Regulatory compliance frameworks, such as HIPAA and PCI-DSS, continue to drive market activity, as organizations strive to meet stringent security requirements.
- Security incident response and digital forensics have become essential components of cybersecurity infrastructure. Threat intelligence platforms and vulnerability management systems help organizations stay informed about potential risks and mitigate them effectively. Meanwhile, incident response planning and zero trust architecture are gaining traction, as organizations seek to minimize the impact of potential security breaches. Network security protocols, such as SSL/TLS and IPsec, are being leveraged to secure data transmission and protect against intrusion attempts. Cybersecurity awareness training is also a priority, with organizations investing in employee education to prevent human error and strengthen their overall security posture.
- Physical security controls and cryptographic algorithms continue to play a role in securing government data, while ransomware mitigation strategies and malware analysis techniques help organizations respond to and recover from cyber attacks. Cloud security posture and risk assessment methodologies are also crucial considerations, as more data and applications move to the cloud. Penetration testing services and multi-factor authentication are essential tools for identifying vulnerabilities and securing access to sensitive information. Meanwhile, intrusion detection systems and cybersecurity insurance help organizations detect and respond to potential threats in real-time and manage their risk exposure. In summary, the US government cybersecurity market is characterized by ongoing innovation and a focus on proactive security measures.
- Organizations are continually adapting to new threats and evolving regulatory requirements, investing in a range of solutions to protect their data and maintain compliance.
What are the Key Data Covered in this US Government Cyber Security Market Research and Growth Report?
-
What is the expected growth of the US Government Cyber Security Market between 2025 and 2029?
-
USD 4.18 billion, at a CAGR of 6.1%
-
-
What segmentation does the market report cover?
-
The report segmented by End-user (US intelligence community, Department of homeland security, and Department of defense), Deployment (On-premises and Cloud-based), Product (Services and Solutions), Security Type (Network Security, Endpoint Security, Application Security, and Cloud Security), and Threat Type (Cyber-Attacks, Data Breaches, Espionage, and DDoS Attacks)
-
-
Which regions are analyzed in the report?
-
US
-
-
What are the key growth drivers and market challenges?
-
Firewall as disruptive threat deception strategy, High cost of deploying cyber security solutions
-
-
Who are the major players in the Government Cyber Security Market in US?
-
Key Companies BAE Systems Plc, Booz Allen Hamilton Holding Corp., Cisco Systems Inc., CyberArk Software Ltd., Cyderes, Dell Technologies Inc., DXC Technology Co., Fortinet Inc., Fortra LLC, General Dynamics Corp., International Business Machines Corp., Leidos Holdings Inc., Lockheed Martin Corp., Northrop Grumman Corp., NXTKey Corp., Proofpoint Inc., RTX Corp., SolarWinds Corp., The Boeing Co., and Trend Micro Inc.
-
Market Research Insights
- The government cyber security market in the US is a significant and dynamic sector, encompassing various solutions and services to safeguard critical infrastructure and data. Two key areas of investment include incident management processes and security architecture design. According to industry estimates, the incident management market is projected to reach USD11.5 billion by 2025, growing at a CAGR of 12.5%. In contrast, the security architecture design market is anticipated to expand at a CAGR of 14.2% and reach USD15.6 billion by 2026. These figures underscore the importance of effective incident response and proactive security measures in the government sector.
- Other essential components of the market include compliance audits reports, intrusion prevention systems, encryption key management, vulnerability scanning tools, threat hunting strategies, and more. These solutions employ ethical hacking methods, encryption key rotation, disaster recovery planning, antivirus software deployment, system hardening techniques, malware signature updates, password management systems, cloud security controls, security operations centers, security awareness programs, business continuity management, security metrics dashboards, forensic data analysis, risk mitigation strategies, identity governance systems, access control policies, and network segmentation techniques.
We can help! Our analysts can customize this us government cyber security market research report to meet your requirements.